Within GCHQ, there is a division called the National Cyber Security Centre (NCSC). Given that GCHQ is the UK equivalent of the NSA, you can rest assured that this organisation will know a thing or two about computer security… The role of the NCSC is to provide guidance to the country about how to keep all things computerised, safe.
Naturally, the advice is pretty generic and whilst it may point out a problem, it may not go quite into the specifics about how to remedy the problem. I have decided to write a small series of articles that put the good advice from the NCSC into usable, real world solutions.
This is the first one and is centred around some of the NCSC advice for Small Businesses.
The first item is backup
The NCSC advises that not only should you take backups but that you should test them. This is very good advice and let’s be honest here, most people do not test their backups. In a tight spot, a backup can be the difference between still having all your data and not. If you are in any doubt about your backups, go and ask your IT person whether your business has tested its backup restore ability recently. Don’t just assume that all is well, you know what they say about the word “assume”…
On the subject of backup, have a look at this chart as you may not be backing up in a sensible way:
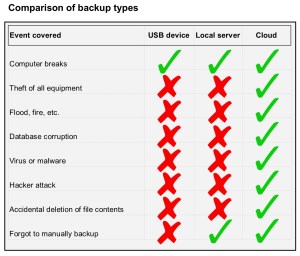
Brigantia recommends using one of the following solutions: BackupPro, Data Deposit Box or MozyPro.
The second item is about preventing malware damage
Malware is a very broad term and includes ransomware, viruses and pretty much everything that is bad that can get onto computers. The NCSC advises the following:
• Use security software;
• Patch all your software with updates when they become available;
• Control access to removable media such as USB sticks and SD-Cards;
• Use your firewall to control access.
All of these points are crucial to your network security. For the first point, you don’t just need an antivirus program, you need anti-hacker-ware too. You need something that watches the data traffic in addition to looking at the files, you need Heimdal Security. Heimdal will run alongside your antivirus software if you wish, but there is the option to use the Heimdal antivirus module if you prefer.
The second point, the application of patches, this should be automated. Again, Heimdal to the rescue as this program will quietly patch your software in the background without disturbing your users. This means that if a new vulnerability appears in your chosen PDF reader for example, Heimdal will just patch it on all your machines within hours of the patch being released so that hackers can’t use it to gain access to your network.
All media from DVDs to USB sticks to camera cards can introduce malware to your network without the knowledge of the user. All media ports should be disabled on your network as a safety precaution.
Use of a decent firewall is highly advisable and investigating a managed firewall would be time well spent as this way, your network will be much tougher to hack into from the outside.
The NCSC should be praised for its efforts in publishing this advice for small businesses. However, it is always a good policy to speak to an expert to get practical guidance that will work for your business. If you would like to be put in touch with a participating Brigantia partner for help and advice with anything covered in this article, then please call Brigantia on 020 3358 0090 or email partnersupport@brigantia.com.
There will be more NCSC based articles to come, please watch out for them in the near future!





